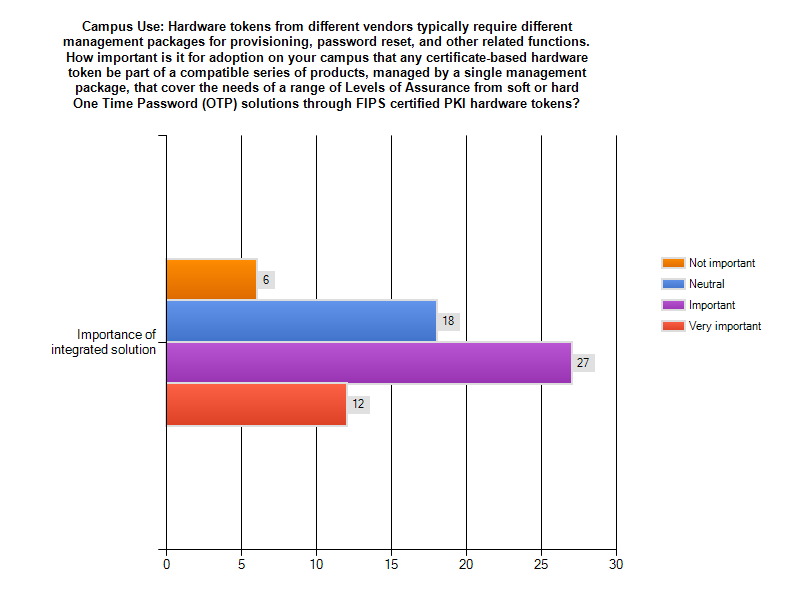
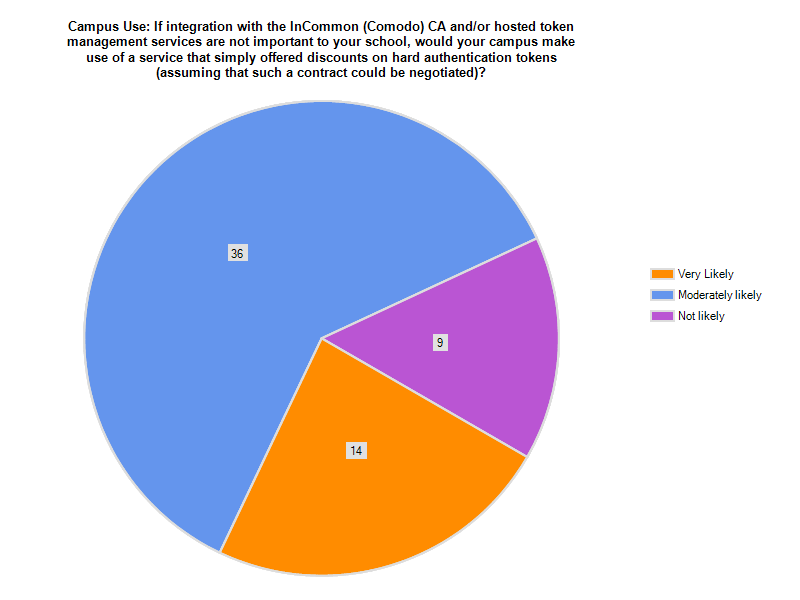
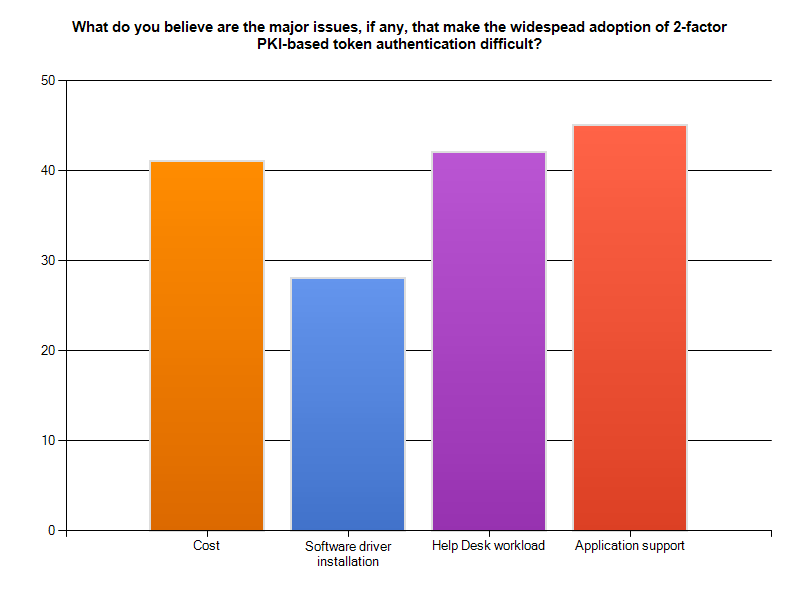
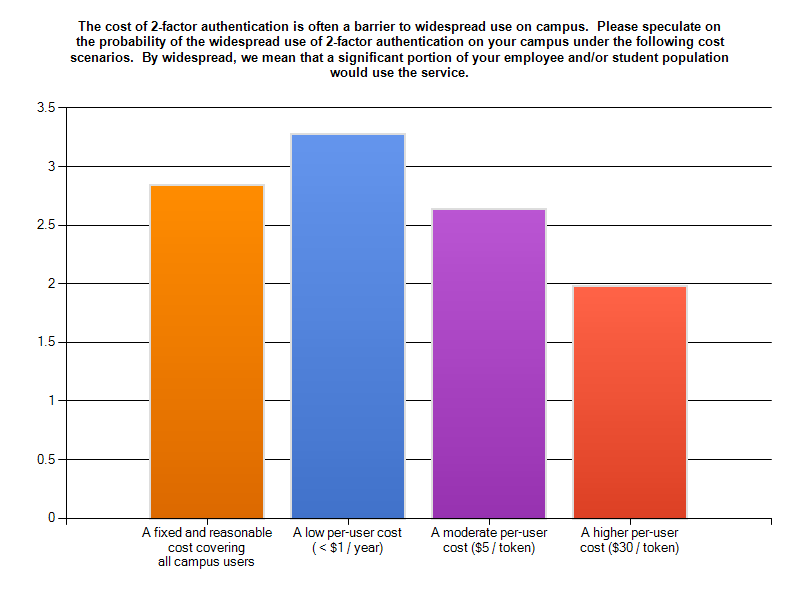
Last reviewed: May July 2015
What Is Two-Factor Authentication?
...
Privacy, and the threat of identity theft, is increasingly a concern as more of personal information finds its way to online applications. In addition, passwords alone can frequently be easily guessed or compromised through phishing or hacking, consequently, no longer providing adequate protection for mission-critical information system and applications containing Personally Identifiable Inforrmation Information (PII), Personal Health Information (PHI), and other confidential information. Some specific concerns:
...
Other requirements for two-factor authentication include Internet banking. For that reason, the Federal Financial Institutions Examination Council (FFIEC) strongly recommends two-factor authentication for consumer online banking services. Specifically, in its Supplement to Authentication in an Internet Banking Environment, under Customer Authentication for High Risk Transactions, it states "Financial institutions should implement layered security, as described herein, utilizing controls consistent with the increased level of risk for covered business transactions. Additionally, the Agencies recommend that institutions offer multi-factor authentication to their business customers."See Client (Personal) Certificates: Should We Be Thinking About Certificate Use Cases or Should We Be Thinking About The Sort of
| Tip | ||
|---|---|---|
| ||
Check out Breaking the Ubiquitous Two-Factor Barrier, presented by Jane Drews (University of Iowa and Quinn Shamblin (Boston University) at the 2015 Security Professionals Conference. For other recent presentations visit access control and identity and access management in the EDUCAUSE library. Learn more about Two-Factor Authentication with Duo Push by visiting the Internet2 NET+ website. |
...
(a presentation at |
...
the 2011 Internet2 Member Meeting |
...
) for questions to ponder when considering deployment of two-factor authentication. |
...
What Technology Is Available?
1.
...
A small device that an individual possesses and controls used to authenticate the individual's identity. It provides the "what you have" component of two-factor authentication since it is used in addition to another piece of evidence (e.g., a password) to prove that individuals are who they claim to be. A token generates a unique code that is combined with an individual's password to create an electronic "ticket" that authenticates the individual and encrypts the transmission to ensure data integrity. Security tokens come in different types. The most common are:
Hardware Tokens: Physical devices small enough to be carried in a pocket or attached to a keychain. They may store digital credentials, a digital certificate, or digitized biometric data (e.g., a fingerprint). Some hardware tokens include input and output intefaces like a small keypad to enter a PIN or a button to generated a key number and a display window to show it. They can also include a Bluetooth wireless interface to enable transfer of the generated key number to a client system.
Hardware tokens also come in different types. Some of the most common are:
- One Time Password (OTP) tokens which generate a new password every so many seconds.
- Challenge-Response tokens, which, given an input (such as a random string of numbers) provide a unique response, which can then be validated by the authenticating server
- USB hard tokens. See description below.
- Other technology solutions such as grid cards or Personal Identification Number (PIN) / Transaction Authentication Number (TAN) systems
| Section | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| |||||||||||||||
|
USB Token: A specific type of hardware token designed to include a Universal Serial Bus (USB) connector. A USB port is standard equipment on today's computers. USB tokens are normally used to store digital certificates. They plug into a computer's USB port and, in some cases, individuals are prompted to enter their PIN to unlock/pass the digital certificate.
Some USB tokens may need drivers to be installed while others may come with self-installing drivers but that only work with certain versions of Windows.
Second Channel Authentication - Mobile Phone-based
Though similar to two-factor authentication but different, second channel authentication allows individuals to use their mobile phone as a security token (i.e., what you have.) A Java application installed on the mobile phone performs the functions normally provided by a security token. Other methods of using the cell phone include using Short Message Service (SMS) messaging, prompting an interactive telephone call, or using standard Internet protocols such as HTTP or HTTPS. Second channel authentication uses a mobile phone via a cellular network in addition to the computing device connected via an IP connection. This authentication method is already in use in online shopping, with Google's version of two-factor authentication built within the Google shopping cart.
See Mobile One-Time-Passwords (OTP), Google Authenticator, and DuoSecurity for information on implementation of OTP via mobile phones. Additional implementation options include:
- SMS push to a preregistered device
- Photograph-the-barcode-on-your-device's screen
- Answer a call made to the individual's mobil phone and hit a specified key
Biometric voice verification
Section border true Column width 30% Advantages:
- Since most users are already carrying smartphones, it may be perceived as an easier or more convenient way to authenticate than using tokens or smart cards
- Compatible with a large number of applications
- Easy to use
Column width 30% Disadvantages:
- Relatively new technology, not as mature but gaining acceptance
- Some confusion exists regarding the levels of two-factor strength of DTMF tones (out of band) vs one-time-passwords (in band) vs SMS (either or) and vendor available options
- The possibility of cell phone cloning or interception
- There may be locations/situations in which the use of smartphones may not be viable or functional (airplanes? basements?) or may be too expensive (e.g., when travelling overseas and paying international rates/roaming rates)
Column width 30% Who Is Using It (this is just a sample list):
2. Security Tokens
A small device that an individual possesses and controls used to authenticate the individual's identity. It provides the "what you have" component of two-factor authentication since it is used in addition to another piece of evidence (e.g., a password) to prove that individuals are who they claim to be. A token generates a unique code that is combined with an individual's password to create an electronic "ticket" that authenticates the individual and encrypts the transmission to ensure data integrity. Security tokens come in different types. The most common are:
Hardware Tokens: Physical devices small enough to be carried in a pocket or attached to a keychain. They may store digital credentials, a digital certificate, or digitized biometric data (e.g., a fingerprint). Some hardware tokens include input and output intefaces like a small keypad to enter a PIN or a button to generated a key number and a display window to show it. They can also include a Bluetooth wireless interface to enable transfer of the generated key number to a client system.
Hardware tokens also come in different types. Some of the most common are:
- One Time Password (OTP) tokens which generate a new password every so many seconds.
- Challenge-Response tokens, which, given an input (such as a random string of numbers) provide a unique response, which can then be validated by the authenticating server
- USB hard tokens. See description below.
- Other technology solutions such as grid cards or Personal Identification Number (PIN) / Transaction Authentication Number (TAN) systems
| Section | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| |||||||||||||||
| |||||||||||||||
| Section | |||||||||||||||
| |||||||||||||||
|
Software Tokens: Non-physical device that is stored on a desktop computer, laptop, Personal Digital Assistant (PDA), or mobile phone. As in the case of hardware tokens, they may store digital credentials or a digital certificate.
USB Token: A specific type of hardware token designed to include a Universal Serial Bus (USB) connector. A USB port is standard equipment on today's computers. USB tokens are normally used to store digital certificates. They plug into a computer's USB port and, in some cases, individuals are prompted to enter their PIN to unlock/pass the digital certificate.
Some USB tokens may need drivers to be installed while others may come with self-installing drivers but that only work with certain versions of Windows.
| Section | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| |||||||||||||||
|
2. Smart Cards
A pocket-sized card, similar to credit card, with embedded integrated circuits that communicate with external devices via a card reader.
Smart cards can be programmed to provide identification and authentication services. The most advanced cards include encryption hardware that uses algorithms that support the NIST standard for Personal Identity Verification (FIPS 201) and/or secure Bluetooth-enabled card readers to link smart cards to users' smart phones but the readers can be expensive.
Similar to USB tokens, they also provide the "what you have" component of two-factor authentication since with a smart card an individual authenticates by using a PIN in combination with a smart card that contains the individual-specific information.
Software Tokens: Non-physical device that is stored on a desktop computer, laptop, Personal Digital Assistant (PDA), or mobile phone. As in the case of hardware tokens, they may store digital credentials or a digital certificate.
| Section | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||||||||
| Section | ||||||||||||||||||||
| ||||||||||||||||||||
| ||||||||||||||||||||
|
3.
...
The use of intrinsic physiological and behavioral characteristics to authenticate a particular individual. Most biometric-based authentication follows a four-step process:
...
Smart Cards
A pocket-sized card, similar to credit card, with embedded integrated circuits that communicate with external devices via a card reader.
Smart cards can be programmed to provide identification and authentication services. The most advanced cards include encryption hardware that uses algorithms that support the NIST standard for Personal Identity Verification (FIPS 201) and/or secure Bluetooth-enabled card readers to link smart cards to users' smart phones but the readers can be expensive.
Similar to USB tokens, they also provide the "what you have" component of two-factor authentication since with a smart card an individual authenticates by using a PIN in combination with a smart card that contains the individual-specific information
...
.
| Section | |||
|---|---|---|---|
| |||
|
...
|
...
|
...
|
- Requires relatively more complex and expensive technology
- Requires calibration through multiple image captures to minimize the probability of erroneous rejection of authorized individuals or erroneous acceptance of unauthorized individuals
- Concerns about accuracy, privacy and security of biometric indicators, and potential inconvenience make user acceptance difficult
- Adds complexity to replacement of compromised credentials (e.g., how do you revise the template created from an individual's iris scan or thumbprint)
- Illness or injury might make it difficult or impossible for individuals to authenticate
- Potential accessibility barriers for disabled individuals
|
4. Biometrics
The use of intrinsic physiological and behavioral characteristics to authenticate a particular individual. Most biometric-based authentication follows a four-step process:
- Create a sample of individuals' biometric characteristics during an enrollment process. A profile of an individual's characteristics can be built based on a specific number of samples given.
- Unique data are extracted from the sample and a template is created.
- The template is compared with a new sample provided during authentication.
Access is determined by matching the features extracted from the new sample with those of the template.
Section border true Column width 50% Advantages:
- Strong second factor
- Meet security requirements of integrity and nonrepudiation when combined with digital signatures
Column width 50% Disadvantages:
- Requires relatively more complex and expensive technology
- Requires calibration through multiple image captures to minimize the probability of erroneous rejection of authorized individuals or erroneous acceptance of unauthorized individuals
- Concerns about accuracy, privacy and security of biometric indicators, and potential inconvenience make user acceptance difficult
- Adds complexity to replacement of compromised credentials (e.g., how do you revise the template created from an individual's iris scan or thumbprint)
- Illness or injury might make it difficult or impossible for individuals to authenticate
- Potential accessibility barriers for disabled individuals
Questions to Ask IF Selecting Biometrics
- Would my institution provide effective notice and an opportunity for meaningful consent prior to collecting a biometric sample?
- Is my institution selecting the most appropriate and least intrusive biometric to address the business need?
- What alternative(s) are acceptable/provided for those who may refuse or are unable to provide the selected biometric image?
- Would my institution be generating and encrypting an alphanumeric identifier from the raw/scanned image and would it be using a unique algorithm to limit the identifier's utility outside of the intended domain?
- Would my institution be retaining only the encrypted, alphanumeric identifier and not the raw/scanned image?
- Would the selected identifier-creation algorithm ensure an adequate level of uniqueness, i.e., can different images produce the same identifier? Corollary: Is absolute uniqueness really critical, especially in situations where the identifier is used in conjunction with a second credential, such as a PIN or password?
- Would my institution be considering or using "no trace" technology rather than embedding the digitized identifier into a microchip or smart card?
- Would institutional staff responsible for capturing and manipulating the raw images and identifiers be appropriately trained on the confidentiality and appropriate use of these data?
- How would my institution appropriately destroy the raw images and/or the identifier once their purpose has been served?
- Would my institution create, implement, and maintain policies and procedures for the collection and management of biometric data? How often would these policies and procedures be audited or assessed regarding changes in technology, best practices, and the legal/regulatory environment?
A number of biometric technologies measure different physiological and behavioral aspects of an individual
| Fingerprint Recognition | Signature Characteristics | Palm Scan | Hand Geometry | Retina Scan | Iris Scan | Keyboard Dynamics | Voice Print | Facial Scan |
Description | Examines the unique ridge endings and bifurcations displayed by friction ridges of an individual's fingerprint | Often referred to as dynamic signature verification (DSV), examines how individuals sign their names | Examines the unique creases, ridges, grooves in an individual's hand. Also scans the fingerprints of each finger. | Examines the length and width of an individual's hand. The system compares the geometry of each finger and the hand as a whole | Examines the blood vessel patterns of the retina on the backside of the eyeball | Examines the colored portion of the eye that surrounds the pupil. The iris has unique characteristics (e.g., colors, rings, etc). | Examines the speed and motion used by an individual when typing a specific phrase | Examines an individual's speech sounds and patterns when saying a sequence of words | Examines facial characteristics of an individual - bone structure, nose |
Questions to Ask IF Selecting Biometrics
- Would my institution provide effective notice and an opportunity for meaningful consent prior to collecting a biometric sample?
- Is my institution selecting the most appropriate and least intrusive biometric to address the business need?
- What alternative(s) are acceptable/provided for those who may refuse or are unable to provide the selected biometric image?
- Would my institution be generating and encrypting an alphanumeric identifier from the raw/scanned image and would it be using a unique algorithm to limit the identifier's utility outside of the intended domain?
- Would my institution be retaining only the encrypted, alphanumeric identifier and not the raw/scanned image?
- Would the selected identifier-creation algorithm ensure an adequate level of uniqueness, i.e., can different images produce the same identifier? Corollary: Is absolute uniqueness really critical, especially in situations where the identifier is used in conjunction with a second credential, such as a PIN or password?
- Would my institution be considering or using "no trace" technology rather than embedding the digitized identifier into a microchip or smart card?
- Would institutional staff responsible for capturing and manipulating the raw images and identifiers be appropriately trained on the confidentiality and appropriate use of these data?
- How would my institution appropriately destroy the raw images and/or the identifier once their purpose has been served?
- Would my institution create, implement, and maintain policies and procedures for the collection and management of biometric data? How often would these policies and procedures be audited or assessed regarding changes in technology, best practices, and the legal/regulatory environment?
A number of biometric technologies measure different physiological and behavioral aspects of an individual
| Fingerprint Recognition | Signature Characteristics | Palm Scan | Hand Geometry | Retina Scan | Iris Scan | Keyboard Dynamics | Voice Print | Facial Scan |
Description | Examines the unique ridge endings and bifurcations displayed by friction ridges of an individual's fingerprint | Often referred to as dynamic signature verification (DSV), examines how individuals sign their names | Examines the unique creases, ridges, grooves in an individual's hand. Also scans the fingerprints of each finger. | Examines the length and width of an individual's hand. The system compares the geometry of each finger and the hand as a whole | Examines the blood vessel patterns of the retina on the backside of the eyeball | Examines the colored portion of the eye that surrounds the pupil. The iris has unique characteristics (e.g., colors, rings, etc). | Examines the speed and motion used by an individual when typing a specific phrase | Examines an individual's speech sounds and patterns when saying a sequence of words | Examines facial characteristics of an individual - bone structure, nose ridge, eyes width, forehead size, etc. |
Accuracy | High accuracy level, | Low accuracy level |
| Medium/ Low accuracy level despite highly stable pattern over individual life | The most accurate biometric authentication | The second most accurate biometric authentication. Iris remains unchanged throughout life so iris scan has longer useful life. | Low level of accuracy. Subject to significant variances due to changes of behavior and posture | Medium accuracy level. Can be impacted by circumstances like a cold | Medium / low accuracy level. Pretty good at full frontal views but has problems with angle views, profiles, and varying facial expressions |
User acceptance | Average acceptance though it is the most used and most practical biometric | Very high acceptance level. The signature is the most common form of authentication in the paper world | Average acceptance | High acceptance | Least level of user acceptance | Average acceptance | High acceptance | High acceptance | Average acceptance |
Relative Cost | Medium / Low | Medium |
| Medium | High | High | Low | Medium | Medium |
Application interface | Scanner. Easy to use and require little space | Optic pen and touch panel. More sophisticated devices can measure: | Scanner | Scanner. Easy to capture but system requires large physical space | Reader. Requires direct contact with a cup reader | Reader. Does not require direct contact with the reader | Keyboard | Microphone or telephone. Commonly available sensors Hands-free and eyes-free operation | Camera |
Special Requirements |
| Requires individuals to sign their name with a special pen on a sensitized reader or pad |
|
|
| Acquisition of iris image requires more training than most biometrics |
|
|
|
Privacy Concerns | Privacy concerns of criminal implications |
| Same as fingerprint |
| Can reveal personal medical conditions like high blood pressure and pregnancy | None. Does not reveal personal medical conditions |
|
|
|
Sources: The Biometrics Consortium; The Biometrics Research Group; Biometrics.gov Biometrics Overview; and James Michael Stewart, Ed Tittle, Mike Chapple "CISSP Study Guide", Third Edition
4. Second Channel Authentication - Mobile Phone-based
Though similar to two-factor authentication but different, second channel authentication allows individuals to use their mobile phone as a security token (i.e., what you have.) A Java application installed on the mobile phone performs the functions normally provided by a security token. Other methods of using the cell phone include using Short Message Service (SMS) messaging, prompting an interactive telephone call, or using standard Internet protocols such as HTTP or HTTPS. Second channel authentication uses a mobile phone via a cellular network in addition to the computing device connected via an IP connection. This authentication method is already in use in online shopping, with Google's version of two-factor authentication built within the Google shopping cart.
See Mobile One-Time-Passwords (OTP) and Google Authenticator for information on implementation of OTP via mobile phones. Additional implementation options include:
- SMS push to a preregistered device
- Photograph-the-barcode-on-your-device's screen
- Answer a call made to the individual's mobil phone and hit a specified key
Biometric voice verification
Section border true Column width 50% Advantages:
- Since most users are already carrying smartphones, it may be perceived as an easier or more convinient way to authenticate than using tokens or smart cards
- Compatible with a large number of applications
- Easy to use
Column width 50% Disadvantages:
- Relatively new technology, not as mature but gaining acceptance
- Some confusion exists regarding the levels of two-factor strength of DTMF tones (out of band) vs one-time-passwords (in band) vs SMS (either or) and vendor available options
- The possibility of cell phone cloning or interception
- There may be locations/situations in which the use of smartphones may not be viable or functional (airplanes? basements?) or may be too expensive (e.g., when travelling overseas and paying international rates/roaming rates)
Additional Resources
- Leveraging Certificates for Increased Security, Presentation at the Internet2 Fall Member Meeting, 2011
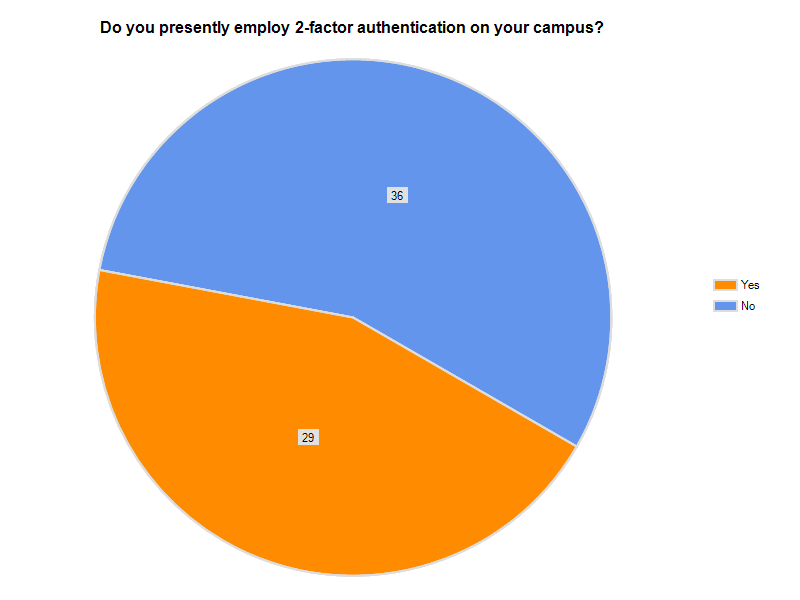
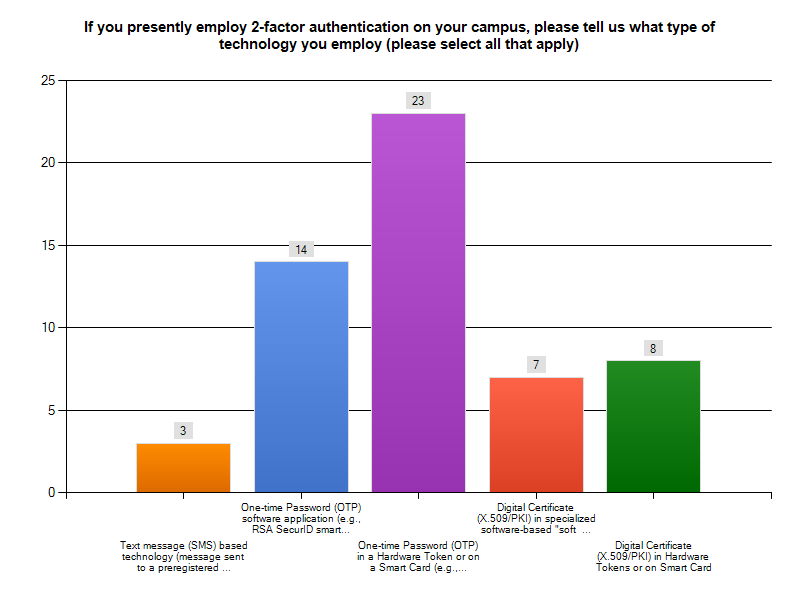
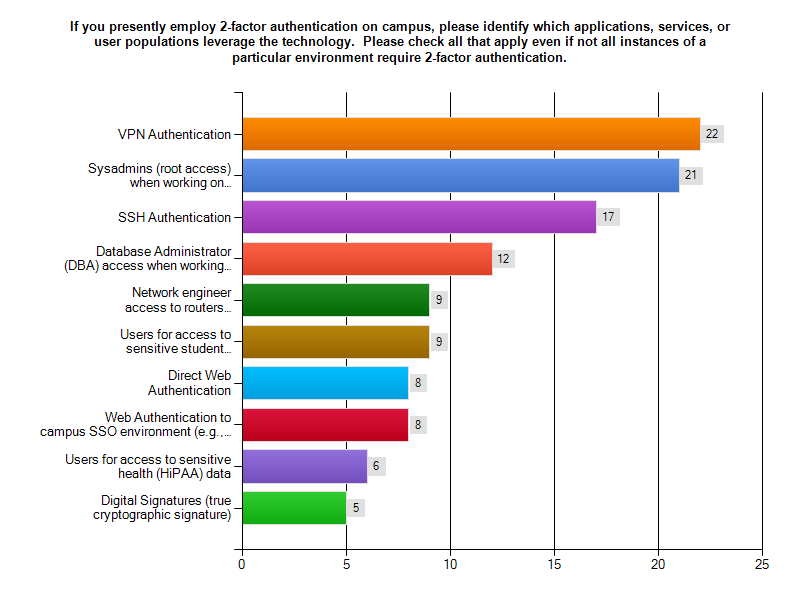
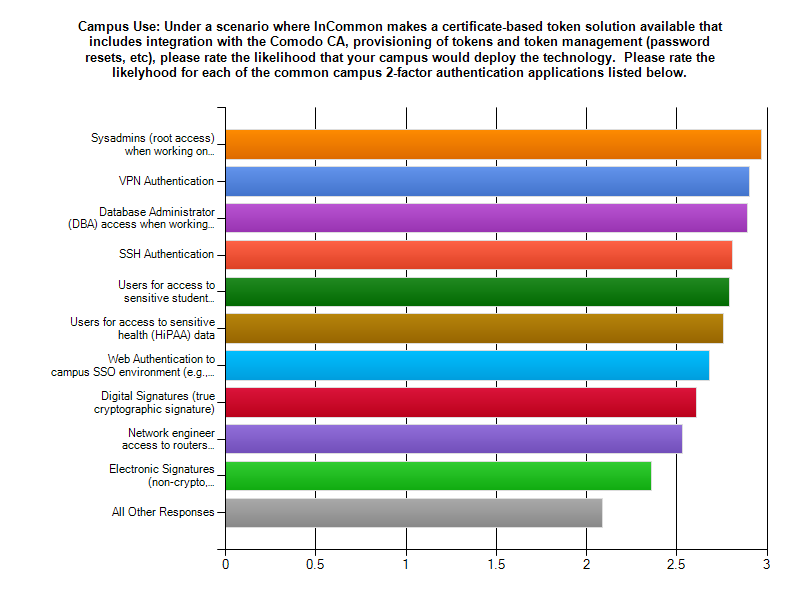
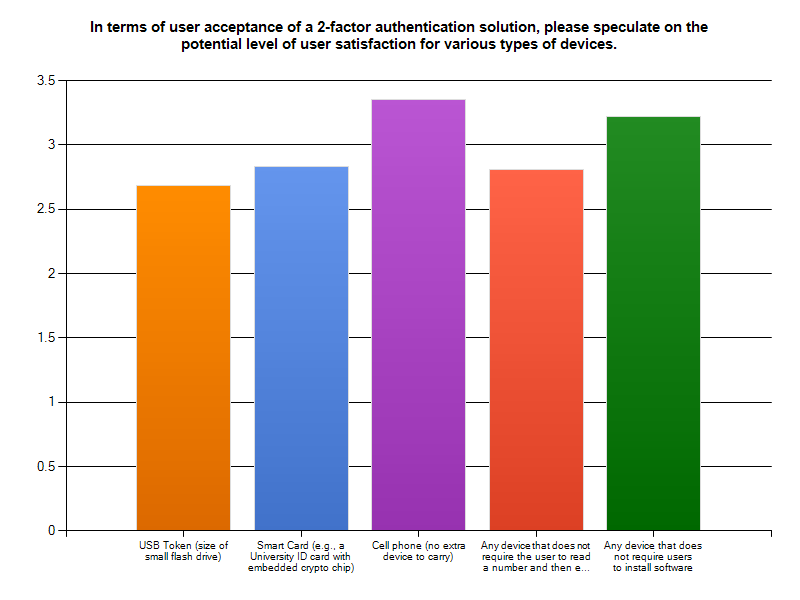
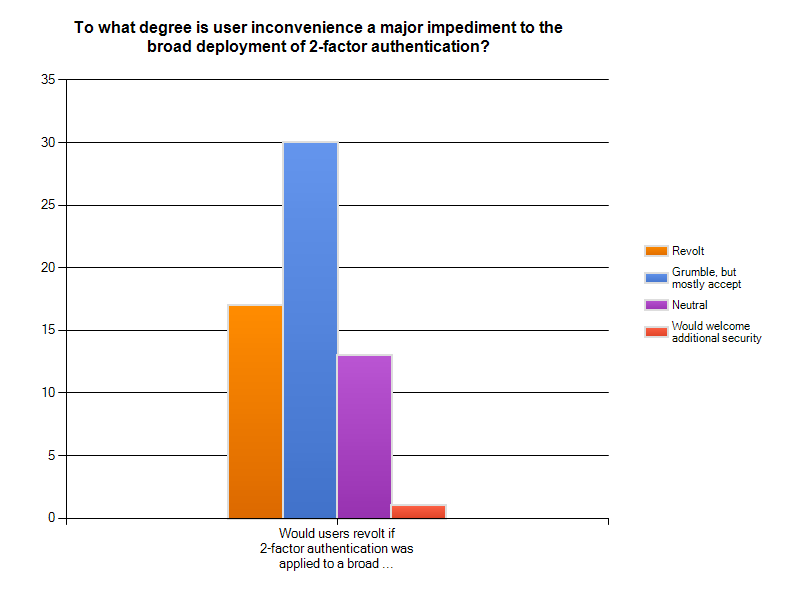
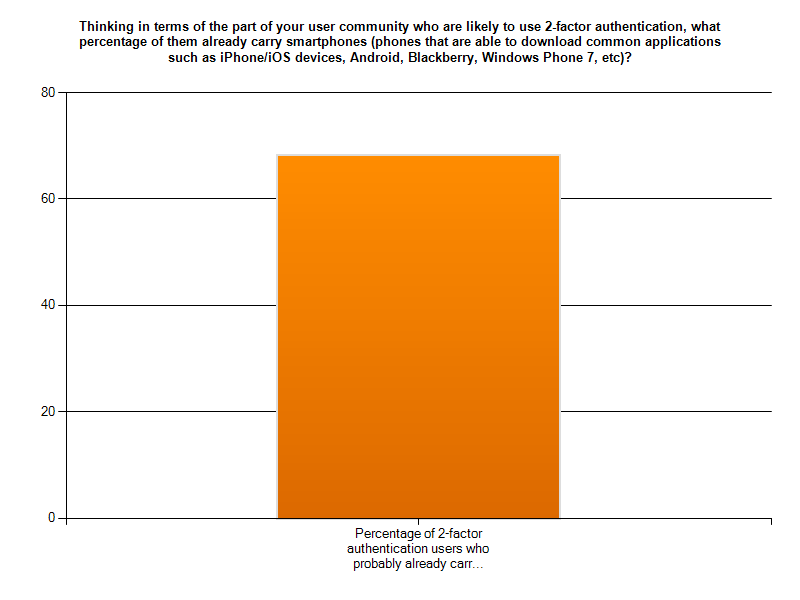
Results from the 2011 Internet2/InCommon Survey on Campus Use of Two-Factor Authentication
Survey Demographics
Name | Count | Average | Median | Min | Max |
Employees | 67 | 9,082 | 6,000 | 500 | 40,000 |
Students | 57 | 27,500 | 25,000 | 1,800 | 107,160 |
2-factor campus users | 29 | 775 | 175 | 4 | 8,000 |
Annual Cost ($) | 23 | 18,574 | 10,000 | 0 | 75,000 |
with angle views, profiles, and varying facial expressions | |||||||||
User acceptance | Average acceptance though it is the most used and most practical biometric | Very high acceptance level. The signature is the most common form of authentication in the paper world | Average acceptance | High acceptance | Least level of user acceptance | Average acceptance | High acceptance | High acceptance | Average acceptance |
Relative Cost | Medium / Low | Medium |
| Medium | High | High | Low | Medium | Medium |
Application interface | Scanner. Easy to use and require little space | Optic pen and touch panel. More sophisticated devices can measure: | Scanner | Scanner. Easy to capture but system requires large physical space | Reader. Requires direct contact with a cup reader | Reader. Does not require direct contact with the reader | Keyboard | Microphone or telephone. Commonly available sensors Hands-free and eyes-free operation | Camera |
Special Requirements |
| Requires individuals to sign their name with a special pen on a sensitized reader or pad |
|
|
| Acquisition of iris image requires more training than most biometrics |
|
|
|
Privacy Concerns | Privacy concerns of criminal implications |
| Same as fingerprint |
| Can reveal personal medical conditions like high blood pressure and pregnancy | None. Does not reveal personal medical conditions |
|
|
|
Sources: The Biometrics Consortium; The Biometrics Research Group; Biometrics.gov Biometrics Overview; and James Michael Stewart, Ed Tittle, Mike Chapple "CISSP Study Guide", Third Edition
...
Questions or comments?
Contact us.
...