Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Anchor | ||||
|---|---|---|---|---|
|
| Info | ||
|---|---|---|
| ||
| Anchor | ||||
|---|---|---|---|---|
|
Welcome to the HEISC Information Security Guide!
Wish you didn't have to reinvent the wheel every time you start a new project, policy, or function? Looking for a guide that will provide you with a variety of information and resources relevant to higher education information security programs? You're in the right place!
The Information Security Guide is mapped to several popular standards, including ISO/IEC 27002:2013, NIST, HIPAA, COBIT, PCI DSS, and the federal Cybersecurity Framework. There are currently 17 chapters on information security, privacy, identity and access management, governance, risk, and compliance.
What makes the guide so unique is that resources and content included in the chapters are provided by higher education information security and privacy professionals. You'll find hot topics, toolkits, case studies, best practices, and recommendations for 'getting started' that will help you jumpstart key information security and privacy initiatives or programs at your institution!
Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Executive Overview of the Guide
Campus leaders are grappling with how to effectively manage and understand challenges and issues associated with information security and privacy. They also have an interest in knowing how other campuses are handling information security and privacy risks and challenges. It's absolutely critical to gain executive support in order to achieve information security and privacy goals and objectives. By using the guide in the development, implementation, and ongoing maintenance of information security and privacy programs, information security, privacy, and IT professionals can provide assurances that their campuses are using effective practices that are relevant to higher education and adopted by their peers. For additional guidance, see Top Information Security Concerns for Campus Executives & Data Stewards.
Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Organization of the Guide
The Home page is your starting point to explore the wealth of content contained in the guide. To your left, you'll find links to toolkits, hot topics, and guide chapters on high-level topics of interest. You'll also see quick links to assist you with navigating the guide, contributing content, or making comments to help us continue to improve this resource.
In addition, every topic page (chapter) includes:
- A Table of Contents which links to key parts of the page
- A Getting Started section that provides recommendations on how to apply the guidance included in each chapter
- An Overview which describes the general intent of each chapter's topic
- Subtopics with objectives, descriptions and/or implementation suggestions, as well as links to articles, presentations, and institutional case studies or examples
- A comprehensive list of Resources referencing other materials relevant to the topic
- Mappings to popular information security standards
The navigation pane on the left side of every page includes direct links to important resources:
- Home – News and links to key publications and resources
- Welcome to the Guide! – The page you are reading now, which provides an overview of the guide
- Toolkits – A list of resources specifically developed or collected by HEISC volunteers (most are also available from their relevant topic pages; this list collects them all in one place)
- Hot Topics – A list of resources related to topics currently receiving increased attention (most are developed by HEISC volunteers)
- Contribute a Case Study – Provides instructions and submission forms for contributing new case studies, as well as a complete list of case studies included in the guide (case studies are also linked from their relevant topic pages; this list collects them all in one place)
- 17 links connect to topical pages, including new chapters on Privacy and Career and Workforce Development
- Glossary – Provides links to information security terminology and definitions maintained by other organizations
In addition, at the top of every page you will find a "bread crumbs" indication of where you are and how the current page relates to the guide's organizational hierarchy.
Top of page
| Anchor | ||||
|---|---|---|---|---|
|
How to Find Information in the Guide
Using the navigation pane on the left side of the page to access a specific topic (chapter) is often the quickest way to find what you are looking for. However, the search function will very likely help you find the resources you need more easily if you are not sure where information may be located.
Using the search function is fairly straightforward; a couple of tips will make its use even more effective. The Guide is provided as a major section of a generalized wiki that is managed by Internet2 and used for a wide variety of EDUCAUSE and Internet2 topics. Consequently, you can either search for topics within the entire wiki (i.e., the Information Security Guide and all other EDUCAUSE and Internet2 sections) or within just the guide.
Searching the Entire Wiki
As you enter a search term in the search box at the top right of the page, it looks across the entire wiki and starts to show possible search results that have the search term as a part of a document title. If you see a document you are interested in, you can select it and you will be transferred directly to that document. Hovering your mouse over any of the terms will provide a bit more information to aid in selection – e.g., the wiki "space" in which the document resides (in our case, "2014 Information Security Guide"). NOTE: Although the guide URLs include 2014, content is reviewed on a regular basis and most pages have been updated between 2016-2017.
On the other hand, if you simply press return (or click the Search button), the result stack returned will be a list of all documents which include that term anywhere in all the documents across all the topics (spaces) in the wiki and not just from the guide. For example, searching on the term "awareness" will return over 800 results from the entire wiki (as of June 2017), many not really relevant to your search. Searching the term "management" will return over 3,000 results from the entire wiki (June 2017).
The result-stack page(s) will also include a column on the left where you can filter your search to refine the results. Usually, searching will be more effective it you start by using the more advanced search available in the filter box.
Searching within the Information Security Guide
Leave the search box (at the top of the page) empty and press the Search Button. This will take you to a search page with the column on the left where you can filter your search to obtain a more refined result. To restrict your search to just the guide, choose "All Spaces" on the pull-down menu under Spaces, and select "2014 Information Security..." There are other filters available but we suggest leaving them all at their default values initially.
Now, you can type your search term into the search box that is at the top of the page. For example, searching on "awareness" within the "where" of "2014 Information Security..." (June 2017) returns a much more manageable result stack of just over 100; searching for "management" with the same "Where" filter will return a result stack of just over 140 (June 2017).
Important Searching Note
Searches will automatically include other words with the same root. For example, the "awareness" search will also include the word "aware" as a part of the search and the "management" search will include the words "manage", "manager", and "managers" as a part of its search.
Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Providing Feedback and Suggestions
The Information Security Guide is a living document, constantly being updated and improved. Resources are continuously added or updated through the work of various information security and privacy professionals volunteering in working groups of the Higher Education Information Security Council (HEISC). Our volunteers cannot fully cover all relevant topics for all information security and privacy professionals on all of the EDUCAUSE and Internet2 member campuses. That is why we ask that you share your expertise by providing feedback; we depend upon the feedback of our readers to keep the guide updated, relevant, and timely.
This can be accomplished by clicking on the " Contact Us" link near the bottom of each page or by sending e-mail to security-council@educause.edu.
Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Description of Case Studies
Case studies are descriptions of real-world, practical, proven solutions to information security challenges implemented by one or more institutions. The intent of these case studies is to provide ideas for approaches which may be adopted or adapted to another institution's particular situation.
By filling in a relatively simple form, a case study is written up and submitted to the Higher Education Information Security Council (HEISC). Once received, it is typically reviewed by one or more of the HEISC working groups. This vetting process gives the institution submitting the case study an opportunity to answer questions or add content that enhances its value.
Instructions for submitting a case study, as well as a complete list of case studies currently available throughout the guide, are available on the Case Study Submissions page.
Submitting a case study not only documents a successful institutional approach to information security, as well as providing useful guidance to other institutions, it also gives the author(s) the opportunity to publish.
Top of page
Questions or comments?
Contact us.
Except where otherwise noted, this work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License (CC BY-NC-SA 4.0).
| Tip | ||
|---|---|---|
| ||
As |
an EDUCAUSE member, you have access to vast resources that can help you make informed decisions, network with peers, and advance your knowledge and career. |
Learn more about some of the top tools and most popular resources |
by visiting |
our Cybersecurity Member Orientation page. 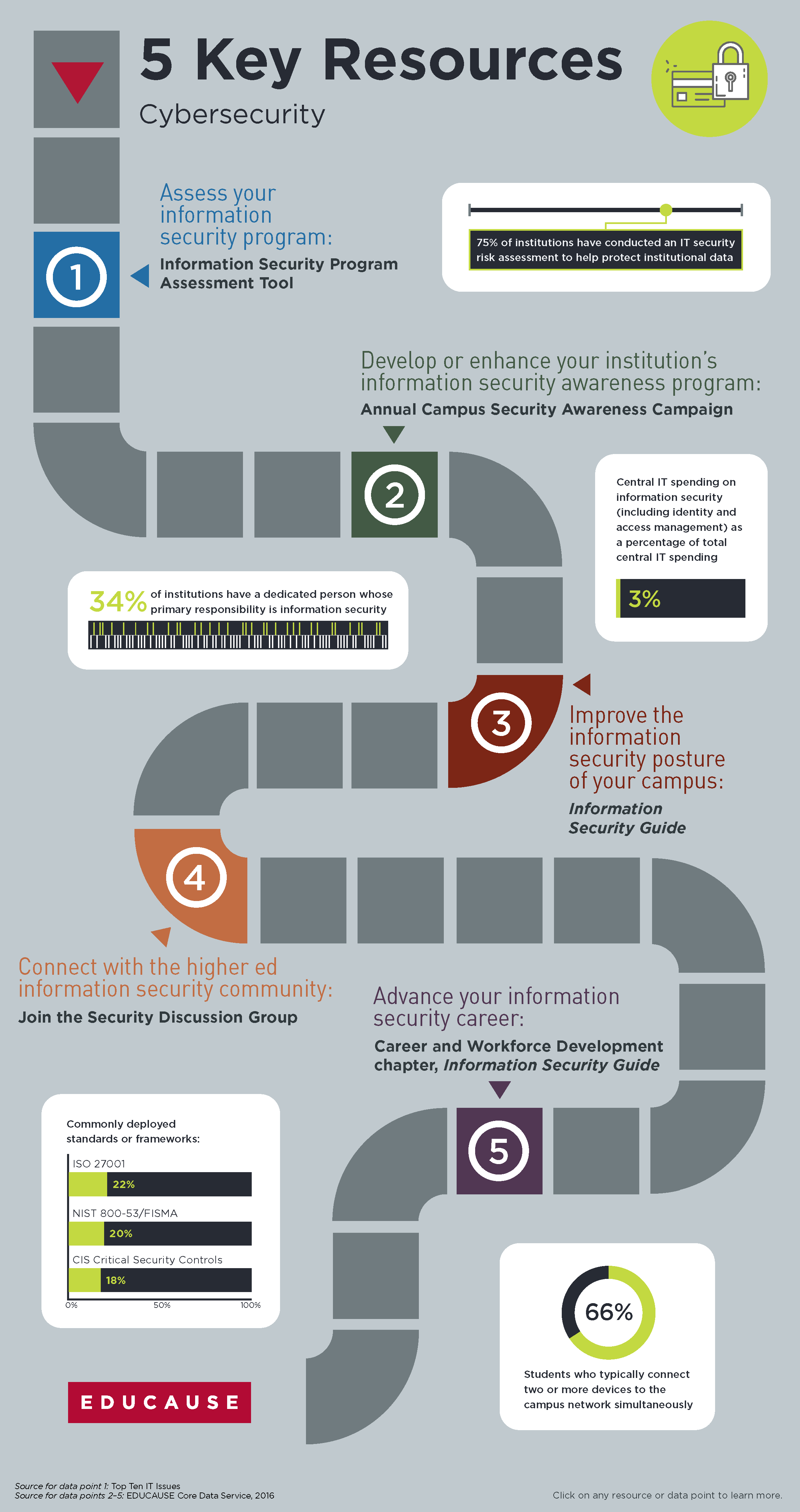 Image Modified Image Modified |