...
Purpose:
The EDUCAUSE/Internet2 Higher Education Information Security Council (formerly the Security Task Force) risk assessment / management framework is intended to provide high-level guidance for an effective cyber-risk assessment and management process for institutions of higher education. It is intended to provide a model process which can be adapted, as needed, for any institution regardless of size, funding model, or culture.
Background and overview:
In virtually every aspect of education, research, and administration there is an increased reliance on digital information and the technologies that support it. With this comes an increasing level of responsibility to protect these information assets from accidental or malicious exposure or damage. In light of current and pending federal and state legislation, it is imperative for universities to recognize that information risk management must be part of their strategic and continuity planning.
Risk management is the ongoing process of identifying these risks and implementing plans to address them. Risk is determined by considering the likelihood that known threats will exploit vulnerabilities and the impact they have on valuable assets. Sometimes risk is expressed as a conceptual formula:_ Risk_ = Threat x Vulnerability x Impact.
Risk assessment is the part of the ongoing risk management process that assigns relative priorities for mitigation plans and implementation. It is a large part of the overall risk management process; many of the steps described in this framework focus on the assessment process.
Risk decisions are made all the time, sometimes without deep consideration and may even be based upon intuition. A formalized risk management process can uncover risks that were not anticipated, resolve funding conflicts, and help enhance executive buy-in to security improvements.
| Panel |
|---|
Some risk terms might be confusing. A vulnerability assessment is basically an inventory of all vulnerabilities. It is often thought of as just a technical examination (networks scanning, etc) but a complete vulnerability assessment would include all manner of vulnerabilities - physical, process, etc. The risk assessment considers those vulnerabilities in light of the other aspects of the risk formula - threats and impact (which includes the concepts of both asset and value) so that the potential mitigations that might be applied can be prioritized. Risk management is actually doing all that plus actually mitigating the selected vulnerabilities, measuring the outcome of the process, and repeating the process again and again. Often, the number of assets potentially at risk exceeds the resources available to manage them. It is therefore extremely important to know where to apply available resources to mitigate the highest priority risks in an efficient and cost-effective manner. It is also important to balance security with usability. |
Using the Framework:
Risk assessment and management scope may vary. For instance, assessments may be conducted as part of the planning and purchasing process for significant projects or systems. Assessments may also be conducted in response to IT security incidents to help ensure incidents do not recur. They may also be conducted on some regular, periodic basis to assure ongoing compliance and up-to-date security measures.
Moreover, institutions vary in many ways including size, complexity, classification, culture, private/public, and so on. The depth and focus of assessments conducted will often depend upon these and other local considerations. While it is certainly possible to follow every step in every process in every phase of this framework (and many institutions do so) the intent of the framework is to be adaptable to local requirements. It is expected that institutions may decide to combine certain steps or processes to streamline the framework for specific purposes.
Especially for comprehensive risk assessments at large institutions, depth might need to be balanced with feasibility to complete the assessment in a reasonable time frame. Resisting the urge to be overly comprehensive is important because assessments that take longer than a few months to complete may lose value as data becomes stale. Here are some tips to help manage large comprehensive assessments.
- Aggregate resources into similar groups and assess the group rather than individual resources. For example, rather than assess each workstation, aggregate similar workstations in to a group and assess them as a group.
- Avoid straying from the process. Resist mission creep.
- Focus on most critical assets
- The most confidential IT resources
- IT resources with highest availability requirements
- IT resources with the most strict integrity requirements
- IT resources that are critical to the mission and function of the unit
- IT resources that are most difficult to replace
- IT resources that are most expensive to replace
Regardless of the assessment scope or local modifications to the process, all four phases of this framework will always apply.
Other points to consider:
- Risk assessment should be thought of as an ongoing process, not as a one-time project. The process is described as a set of steps that are continually repeated. At the outset, however, there is a start-up process that usually is not repeated.
- Conducting a university-wide information risk assessment is a process that will require strong commitment from upper administration and collaboration between cross-functional units. Assessing information risks is a management issue, not a technology issue; therefore, to be most effective, the process should be considered the responsibility of all members of management. An effective university information risk assessment needs to become a part of the culture of the university community, involving not only IT-staff but also all key staff, administrators, faculty, and students. Education and awareness efforts should be aimed at all of these constituencies.
- Due to the complexities of a university environment, a university-wide information risk assessment requires planning and, more importantly, a strategy that systematically increases the scope of the information risk assessment until it encompasses all university areas.
- A sound risk management program can serve as the basis for prioritizing and resolving possible funding conflicts.
| Panel |
|---|
Visit the EDUCAUSE resource list of Risk Assessment Tools to learn more about other risk assessment materials and products. |
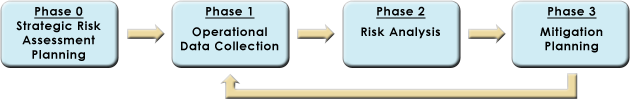
Phase 0: Strategic Risk Assessment Planning (a one-time process)
...
- Determine the criteria to establish for evaluating threat probability and impact.
- Determine the criteria to establish for evaluating vulnerabilities and controls.
Phase 1: Operational Data Collection
...
- Identify key technology components of critical assets for technical evaluation.
- Determine evaluation approach.
- Run evaluation tool(s) on selected technology components.
- Summarize results.
Phase 2: Risk Analysis
...
- Identify risks.
- Create profiles that show a consolidated view of each risk.
- For each risk profile, compose a risk statement.
Phase 3: Mitigation Planning
...
- Evaluate mitigation progress and success.
- Document improvements to risk assessment procedures.
- Plan the next risk assessment.
...
Questions or comments?
Contact us.
...