| Anchor | ||||
|---|---|---|---|---|
|
Table of Contents
- Information Security Aspects of Business Continuity ManagementGetting Started | Information Security Aspects of Business Continuity ManagementOverview | Information Security Aspects of Business Continuity ManagementResources | Information Security Aspects of Business Continuity ManagementStandards
- Information Security Continuity (ISO 17.1)Information Security Aspects of Business Continuity Management
- Redundancies (ISO 17.2)
| Anchor | ||||
|---|---|---|---|---|
|
| Tip | ||
|---|---|---|
| ||
Measures must be taken to ensure the integrity, security, accuracy, and privacy of all systems and data. Such measures include adherence to all governmental regulations and directives. As major disasters have brought acute awareness to campuses, higher education institutions recognize the need for extensive planning and coordination to assure preparedness by developing, testing, and refining plans to handle all types of disruptions to normal services. Use the following steps to get started with a business continuity plan.
A well prepared institution should develop a plan addressing all key services and their administration, delivery, and support. This document presents guidance for institutions considering or embarking on the development of a plan, including commitments, procedures, technologies, resources, methodologies, and communications essential to planning development, support, and deployment. Sections below address the special needs of varied aspects of a plan. |
Information Security Aspects of Business Continuity ManagementTop of page
| Anchor | ||||
|---|---|---|---|---|
|
Overview
Colleges and universities are vulnerable to a variety of natural and man-made emergencies, disasters, and hazards. Recognizing that not all events can be prevented and some risks may be deemed acceptable, proper planning is essential to maintain or restore services when an unexpected or unavoidable event disrupts normal operations.
...
A fire in a building with critical resources would prohibit normal functioning in a localized facility.
An electrical power loss may cover several states or an extended time period. The northeastern states experienced an extended power loss during and after an unusual October 2011 snow/ice storm, Super Storm Sandy, and the numerous blizzards/ice storms/fires/floods of recent years. Outages of some kinds lasted nearly a month in some place; others are still in effect over a year later.
Floods, massive fires, blizzards, tornadoes, hurricanes, tsunamis, earthquakes, pandemics, ice storms, or mud slides that results in evacuations and inaccessibility to critical resources.
A criminal activity or terrorist incident may impact a wide geographic area for an extended period of time.
A pandemic, nuclear, chemical, or biological incident may limit the mobility and accessibility of individuals for extended time periods.
Information Security Aspects of Business Continuity Management of Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Information Security Continuity (ISO 17.1)
| Panel | ||
|---|---|---|
| ||
Objective: Business continuity planning provides a managed, organized method for the deployment of resources and procedures to assure the continuity of operations under extraordinary circumstances, including the maintenance of measures to assure the privacy and security of its information resources. |
...
Collaborative Information Security Project - Vulnerability Assessments - California State University, San Bernardino
Information Security Aspects of Business Continuity ManagementTop of page
Planning Information Security Continuity
Information security must be an integral part of all institutional policies, procedures, and practices. Information security should also be an integral element of business continuity management systems.
Implementing Information Security Continuity
Business continuity plans must recognize the need to strictly adhere to institutional security and privacy policies and regulations, even while the institution is functioning during extraordinary conditions. Good business continuity plans should be built in accordance with strong institutional security and privacy policies as well as state and federal regulations. This will allow important security and privacy practices to continue to be practiced, even during and after a disruptive event. Such practices should be elements of all planning, implementation, testing, and evaluation efforts.
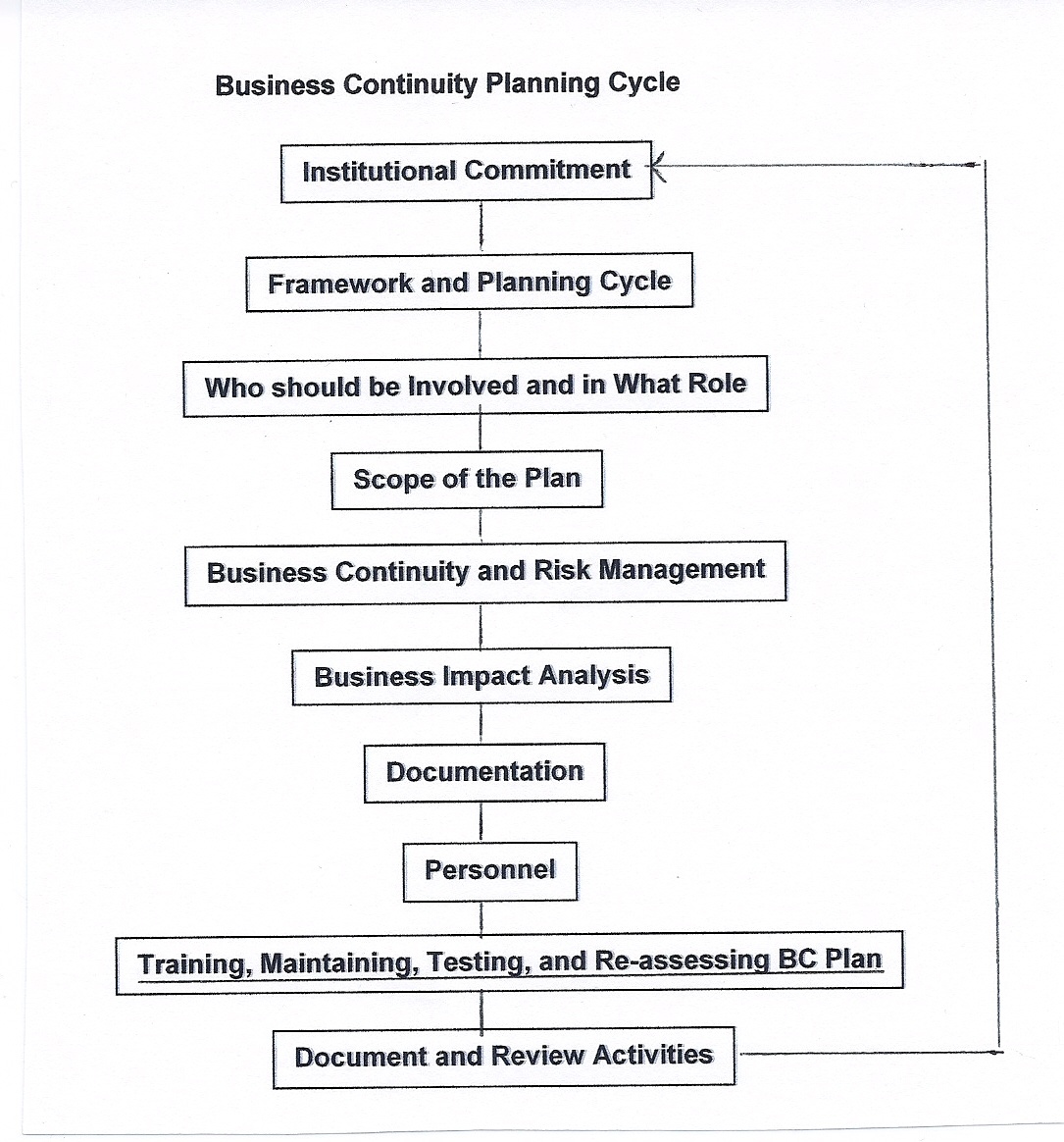
Business Continuity Planning Cycle
Institutional Commitment: Obtain commitment and authority from institutional leadership
...
Information Security Aspects of Business Continuity ManagementTop of page
Framework and Planning Cycle
...
- Seizing the Moment: A New Model for Disaster Recovery at Florida State University
- ISO 27002 Toolkit - Business Continuity
- Business Continuity Planning Process from READY.GOV (US Government)
Information Security Aspects of Business Continuity ManagementTop of page
Who Should be Involved and in What Role - Establish a planning team for each business unit
...
- A Business Continuity Planning Toolkit (2008 presentation + resources)
Information Security Aspects of Business Continuity ManagementTop of page
Scope of the Plan
...
Effective Practice: Incident Response at University of Wisconsin-Madison - University of Wisconsin-Madison
Information Security Aspects of Business Continuity ManagementTop of page
Business Continuity and Risk Management - Perform a risk assessment in each unit
...
Post-9/11 Emergency Response and Business Continuity Changes at Pace University and New York University
Collaborative Information Security Project - Vulnerability Assessments - California State University, San Bernardino
Lessons Learned from RIT's First Security Posture Assessment - RIT
Self-Service/Automated Security Vulnerability Assessment Program - Indiana University
TopInformation Security Aspects of Business Continuity Management of page
Business Impact Analysis - Identify Critical Resources
...
Shared Responsibility for Business Continuity: The Team Approach at UCLA
Information Security Aspects of Business Continuity ManagementTop of page
Documentation
All required information pertaining to the plan, key resources, facilities, management structure, priorities/dependencies, documentation, and personnel should be kept in secure locations which can be physical, virtual, or cloud-based. This information should also be made available to key personnel who will be responsible for coordinating continuity efforts during and after the incident or event.
...
While testing a plan or during an actual deployment, remember to keep track of who is doing what. This can be done via conference calls, texting, alternative web sites, and actual staff reporting in to track all activities as well as make sure that people are safe and getting sufficient food, water, and rest. Communication may be difficult, but it is essential. Not everything will work as scripted, and communicating with other team members may help solve the unexpected or undocumented.
Information Security Aspects of Business Continuity ManagementTop of page
Personnel
People are the key element of the plan. Being able to communicate during a crisis may not be easy due to loss or overloading of infrastructure. Continuity plan leaders or coordinators should be good leaders and managers, capable of keeping the effort organized according to procedures, yet able to be creative when things don't go as planned.
...
Because people are key, it is important to care for their needs as the institution is heavily dependent on their skills and ability to perform. Be cognizant of their needs for food, water, and rest as well as their ability to communicate with their families. Support them as they help the institution get through the crisis.
Information Security Aspects of Business Continuity ManagementTop of page
Communication
Being able to communicate during a crisis is essential. Students, faculty, and staff on campus need to know what is happening as well as what they can/cannot do. Relatives want to know about the safety of individuals on campus. Employees involved in continuity need to know how, when, and where they should report. Continuity plan personnel need to communicate with campus executives on the status of services and resources. Everyone needs to know what they should/should not do and when circumstances are expected to change.
...
Information Security Aspects of Business Continuity ManagementTop of page
Training, Maintaining, and Re-assessing Business Continuity Plans
| Panel | ||
|---|---|---|
| ||
Objective: Business continuity plans must include managed, organized procedures for the development of procedures to assure the continuity of operations under extraordinary circumstances including the maintenance of measures to assure the privacy and security of its information resources. It includes training individuals with responsibilities for the plan's implementation, having regular reviews and updates to keep the plan correct, and for testing the plan to evaluate its feasibility, thoroughness, and effectiveness even under the most unusual of circumstances while maintaining the privacy and security of its information resources. |
...
| Anchor | ||||
|---|---|---|---|---|
|
Redundancies (ISO 17.2)
| Panel | ||
|---|---|---|
| ||
Objective: As a critical element of maintaining continuity of services, there needs to be adequate redundancy of facilities, people, communications, documentation, training, and services. |
...
Due to the nature of business continuity management, it is essential that all elements of a plan have adequate redundancies available, knowing that some elements may be compromised by the nature of the disruption. Redundancies include cross training of personnel, alternate facilities at locations that do not share vulnerabilities, redundant communications methods and providers, power sources, physical access, and more.
Information Security Aspects of Business Continuity ManagementTop of page
BC PLAN - AVOID POTENTIAL SINGLE POINTS OF FAILURE
...
Information Security Aspects of Business Continuity ManagementTop of page
Key Considerations
Data is Essential and Must Be Replicated
Data is more important than hardware. Data should be replicated by a variety of means and should be retrievable as needed. Hardware can always be replaced. Be aware of dependencies between software and data. Cloud services may provide viable options for replication as long as security and privacy are maintained.
Lecture Capture and Delivery for Use During a Pandemic or Biological Emergency
Consider the impact of a pandemic or biological emergency on the delivery of instruction when neither the instructor nor the students are able to be present in the same physical location. There are several alternative means for instructional delivery ranging from videoconferencing to providing previously captured lectures available on demand. Lectures can be streamed to or from campus and alternate locations. Technology can be leveraged to produce audio, video, and screen captures that enable both time and location shifts.
Alternate Sites for Web Hosting
Consider the impact of a hurricane on physical facilities (which become uninhabitable), life-safety issues (evacuations, flooding, disease, lack of potable water and food, etc.), electrical power/network infrastructures, and an extended prognosis for the restoration of "normal operating conditions." A business continuity plan should identify alternative means to be used to provide essential services under such unthinkable circumstance. Services should include means for communicating information on the status and safety of the institution and its people to the rest of the world. Consider contracting for an alternate service for communicating key information with on and off campus people while normal institutional web services cannot be provided.
Availability of Information Processing Facilities
Despite the emergency or disruptive circumstances, information processing facilities must continue to function, be accessible for critical processing, and maintaining the security, integrity, and privacy of information. In creating plans, many variables need to be considered when choosing alternative sites, services, personnel, vendors, power/communication means, and accessibility.
...
Communications facilities and contact information must be as accurate and complete as those used for daily operations. They provide the lifeline for all coordination of communication.
Information Security Aspects of Business Continuity ManagementTop of page
Good Vendor Relationships are Important
...
- Business Continuity After Hurricane Ike: A Tale of Two Schools
- At Least It Wasn't a Football Weekend: The Notre Dame Tunnel Fire
- Hazards and Hurricanes: Hallmarks of IT Readiness, Response, and Recovery
- Fire at OLLU! Business Continuity from an IT Perspective
Information Security Aspects of Business Continuity ManagementTop of page
After the Resumption of Normalcy
...
- All Hazards - An integrated planning approach to all domestic terrorist attacks, major disasters, and other emergencies.
- Business Continuity (also referred to as Continuity of Operations Planning and Service Continuation Planning) - A process for determining an institution's ability to maintain or restore its business and academic services when some circumstance disrupts normal operations.
- Business Impact Analysis - A management level analysis which identifies the impacts of losing resources. This analysis measures the effect of resource loss and escalating losses over time, in order to provide senior management with reliable data upon which to base decisions on risk mitigation and continuity planning.
- Disaster Recovery - A plan for the recovery of information technology resources in the event of a disaster or emergency that generally contains details to ensure systems and communications are restored within a predetermined time frame. The disaster recovery plan is a critical component of the business continuity plan.
- Emergency Response Plan - This includes details for responding to sudden states of danger that require immediate action.
- Pandemic Planning - Preparation in the event that a highly infectious virus, such as the H1N1 or Avian flu reaches pandemic stage.
Information Security Aspects of Business Continuity ManagementTop of page
| Anchor | ||||
|---|---|---|---|---|
|
Resources
| Anchor | ||||
|---|---|---|---|---|
|
Standards
27002:2013 Information Security Management | 800-100: Information Security Handbook: A Guide for Managers | DSS04.02 | Req 12.9.1 | ID.BE-4 | 45 CFR 164.308(a)(7) |
The ISO 27002 Toolkit provides assistance in the development of a business continuity plan. It addresses much of the essential preparation including identification and analysis of priorities, dependencies, contingencies, risk analysis, auditability, and impact analysis. The toolkit includes a framework and checklists to aid in the development, on-going support, and testing of a plan.
Information Security Aspects of Business Continuity ManagementTop of page
...
Questions or comments?
Contact us.
...