| Anchor | ||||
|---|---|---|---|---|
|
Table of Contents
- Information Security Incident ManagementGetting Started | Information Security Incident ManagementOverview | Information Security Incident ManagementResources | Information Security Incident ManagementStandards
- Management of Information Security Incidents and Improvements (ISO 16.1)
| Note |
|---|
If you're currently dealing with a security incident, remember these four basic tips: 1) Don't panic. 2) Do a quick assessment. 3) Report the problem. 4) Determine a course of action. |
...
| Tip | ||
|---|---|---|
| ||
No matter the extent of our defenses, it inevitable that Information Security Incidents will occur. For this reason establishing, periodically assessing, and continually improving incident management processes and capabilities is very important. If you are just getting started in this area of your security program, then the following areas are very useful stepping stones that are covered in this chapter:
|
Information Security Incident ManagementTop of page
| Anchor | ||||
|---|---|---|---|---|
|
Overview
Software complexity, near universal worldwide connectivity, and the criminals determined to profit from these factors, make information security incidents inevitable. The goal of an effective information security incident management strategy is a balance of driving the impact of the incidents down, while processing incidents as efficiently as possible. Good incident management will also help with the prevention of future incidents.
...
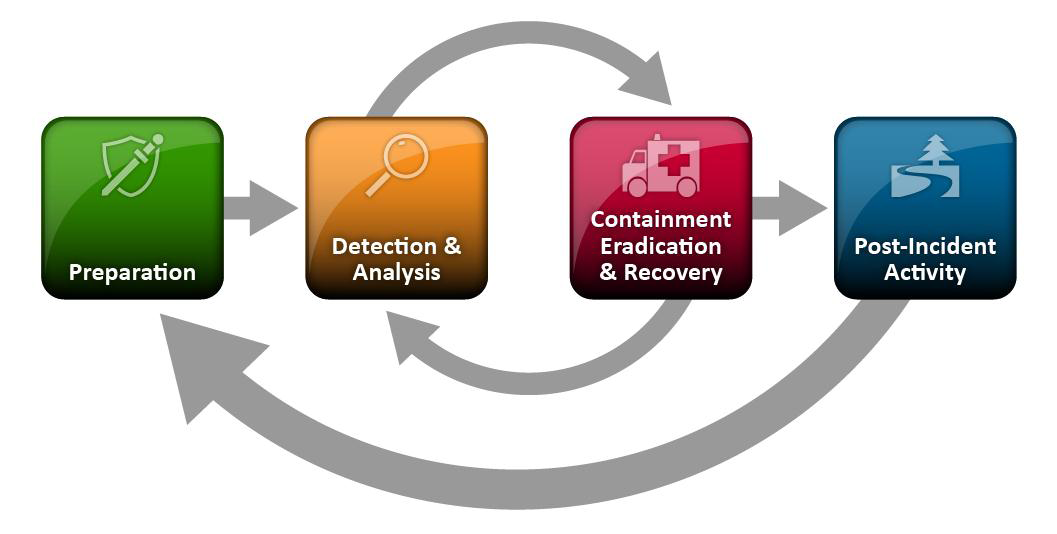
NIST, in their 800-61 Computer Security Incident Handling Guide, describes the "Incident Lifecycle" as:
Information Security Incident Management Top of page
| Anchor | ||||
|---|---|---|---|---|
|
Management of Information Security Incidents and Improvements (ISO 16.1)
| Panel | ||
|---|---|---|
| ||
Objective: To ensure a consistent and effective approach to the management of information security incidents, including communication on security events and weaknesses. |
...
Recommended resource: Cyber Liability Insurance FAQ (2015)
Information Security Incident ManagementTop of page
Responsibilities and Procedures
| Panel | ||
|---|---|---|
| ||
Objective: Ensure personnel are trained and equipped to detect, report, and respond to adverse events, providing the foundation for effective Information Security Incident Management. |
...
- Hacker Techniques, Exploits, and Incident Handling (Security 504)
- Incident Response Management (Management 535)
Reporting Information Security Events
Detection and Reporting
Designing an effective means of the detection of incidents is also essential, using both trained users and trained system administrators, and various technical controls. All members of the community should be trained and comfortable regarding
...
- PaIRS IDS: Finding bad actors without looking at content - EDUCAUSE Security Professionals Conference 2011
- Malware Detection and Mitigation with Passive DNS and Blackhole DNS - EDUCAUSE Security Professionals Conference 2011
Reporting Information Security Weaknesses
Even if a college or university installs a network intrusion detection system or other monitoring systems, the resulting alerts can quickly overload personnel. An effective approach is to use analysis tools to help manage intrusion detection systems and summarize the data. Even when log summarization is used, maintaining and monitoring intrusion detection systems can require resources and technical skill that are beyond some institutions' means. A less expensive alternative to developing your own IDS capabilities is to collaborate with other higher education institutions, helping each other deploy intrusion detection systems and even having a single person monitoring all systems, or to contract for the service with your ISP.
Two major weaknesses of network IDS are that they cannot detect attacks in encrypted traffic and they cannot determine what is occurring within a targeted compromised host. Host-based intrusion detection systems (HIDS) can address both of these issues and can be used to monitor systems processes, file system changes, and log files for suspicious activities. Many commercial endpoint security offerings now include HIDS functionality, and servers can utilize open source monitoring tools. Communicating security alerts through an interface that system administrators use to monitor the status and performance of their systems increases the likelihood that they will notice problems quickly.
Information Security Incident ManagementTop of page
Assessment of and Decision on Information Security Events
| Panel | ||
|---|---|---|
| ||
Objective: Build an effective, timely, repeatable methodology for managing information security incidents that meets legal requirements and is continually improved. |
...
Stages: | Activities: |
Identification and prioritization of incident, and performing a timely assessment of the situation | Determine the scope/impact. The number of users affected, or number of devices, or segments of the network should be considered. Is a single user or account involved? |
| Assess the severity. What is the sensitivity of data involved? What is the criticality of the service, or system, or application? What is the potential for damage or liability? Is there potential for harm? |
| Assess the urgency of the event. Is it an active problem, threat, or event-in-progress? Was the problem discovered after the fact? Is the intrusion "dormant", or completed? Does this involve use of an account rather than a system? Is this involve the safety or privacy of individuals? |
Containment of the event | Does the system need to be removed from the network? Does active memory need to be imaged or captured? |
| Are there user accounts or system-level accounts that need to be disabled or changed? Are there sessions that need to be dropped? |
Investigation of what occurred and how (includes "root cause" analysis) | An incident tracking record needs to be created. If deemed necessary, due to the scope, seriousness, or complexity of the incident, an incident notes log should also be created. |
| Gathering and preserving relevant information should be conducted by trained security personnel. |
| Evaluation of evidence commences. It may be a "forensic" caliber assessment, or a less comprehensive analysis, depending on the type of incident and your institution's policies. Decisions with respect to the appropriate resolution and response should be discussed with decision makers and key stakeholders. |
Response (effect) | Eradication of the problem, and associated changes to the system need to be applied. This includes technical actions such as operating system and application software installs, new or changed firewall rules, custom configurations applied, databases created, backup data restored, accounts created and access controls applied |
| Recovery to a fully operational state always follows appropriate testing or assurance of the system integrity and stability. Effective customer service includes regular communications with stakeholders who may be anxious for recovery. |
| Outcomes, including possible sanctions should be determined. Sanctions, if they are deemed appropriate to the response, may be internal, such as disciplinary action, or they may be external, such as referral to law enforcement. |
Follow up (Improvements) | After incident debriefing. Its important to review the process and how it could have been better, after an incident is closed. This is especially valid for new types of incidents, and particularly severe or costly incidents. |
| Consider policy and process changes. Were any procedures missing, communications unclear, or stakeholders that were not appropriately considered? Did the technical staff have appropriate resources (information as well as equipment) to perform the analysis and/or the recovery? |
| Consider controls improvements, leading to prevention. What can we do to ensure this does not happen again? What improvements can we implement to make our response and recovery more timely? |
Response to information security incidents
Incident Analysis and Forensics
...
- When to Declare an Information Security Incident and How to Respond Once you do - EDUCAUSE Security Professionals conference 2013
- Data Incident Notification Toolkit
- Breaches and a Lawsuit: An Institutions Road to Recovery - EDUCAUSE Security Professionals Conference 2013
- Cyber Liability Insurance FAQ (2015)
Learning from Information Security Incidents
Metrics to Support Improvement
...
- A Guide to Effective Security Metrics
Information Security Incident ManagementTop of page
Collection of Evidence
Recommended Tools and Resources for Incident Handlers
...
- Media (OS and application software)
- Security patches
- Backup images
| Anchor | ||||
|---|---|---|---|---|
|
Resources
| Panel | ||
|---|---|---|
| ||
Campus Case Studies On This Page EDUCAUSE Resources
Initiatives, Collaborations, & Other Resources |
Information Security Incident ManagementTop of page
| Anchor | ||||
|---|---|---|---|---|
|
Standards
27002:2013 Information Security Management | 800-53: Recommended Security Controls for Federal Information | APO11.06 | Req 11 | PR.IP-8 | 45 CFR 164.308(a)(6) |
Information Security Incident ManagementTop of page
...
Questions or comments?
Contact us.
...