JXTA Overview
Objectives
- JXTA ("juxta") was designed to permit implementation of P2P applications using Java.
Characteristics
- Interoperability: Enable peers to find and communicate with each other.
- Platform independence: Independent of programming language, platform, network technology.
- Ubiquity: designed to be implemented on every device (PDAs, servers, etc.).
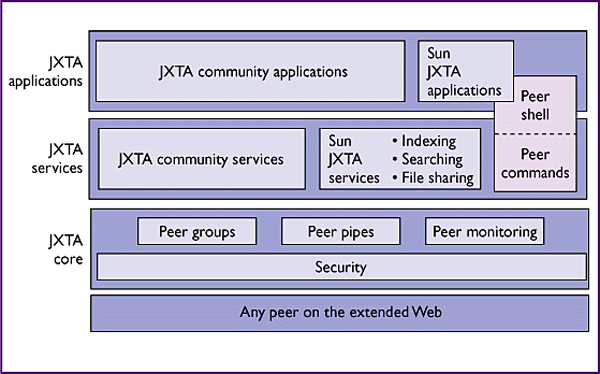
Architecture
- Core: manages communication and peer establishment.
- Middle: handles services (indexing, searching, file sharing).
JXTA Objects and Details
- Each peer is given a 128-bit (not guaranteed to be globally) unique identifier.
- Advertisements: XML documents describing existence of peers, peer groups, pipes, or services.
- Peer: entity that understands all required protocols.
- Messages: base unit of communication, composed of an envelope and a body. Should operate on asynchronous, unreliable, uni-directional transport.
- Peer Group: virtual entity that "speaks" the set of peer group protocols. The World Peer Group includes all.
- Pipes: communication channels for sending and receiving messages. Unidirectional and asynchronous, their endpoints can be moved among peers.
- Point-to-Point Pipe: connects exactly two peers.
- Propagate Pipe: connects multiple peer endpoints.
Protocols
- Peer Discovery: allows peers to find advertisements on other peers; used to find peers, peer groups, advertisements.
- Peer Resolver: allows a peer to send and receive generic search queries.
- Peer Information: allows a peer to learn capabilities and status of other peers.
- Peer Membership: allows a peer to fetch membership requirements, and apply for, update, or cancel memberships.
- Pipe Binding: allows a peer to bind a pipe advertisement to a pipe endpoint; indicates where messages actually go when traversing a pipe.
- Endpoint Routing: allows a peer to query a peer router for available routes in order to send a message to a destination peer.
Discovery Mechanisms
- LAN-based: broadcast.
- Peer can receive invitation message that tells about other peer.
- Peer A can query another peer B about the peers that B knows about.
- Rendezvous peer can act as source of information (directory) about peers.
Security
- Hash, symmetric (RC4) and assymetric (RSA) algorithms.
- PAM-like authentication framework.
- Password-based login scheme.
- Access control mechanism based on peer groups, where members share everything.
- Transport mechanism based on SSL/TLS.
Adapted from Jose M. Vidal (http://jmvidal.cse.sc.edu/talks/jxta/).